Microsoft Patch Nukes Bad Intel Firmware Fix
How bad does a third-party fix have to be for Microsoft to issue a rare, weekend update that helps IT administrators disable it?
Intel issued a firmware fix for variant 2 of the trio of chip security vulnerabilities known as Meltdown and Spectre (see Expect More Cybersecurity 'Meltdowns').
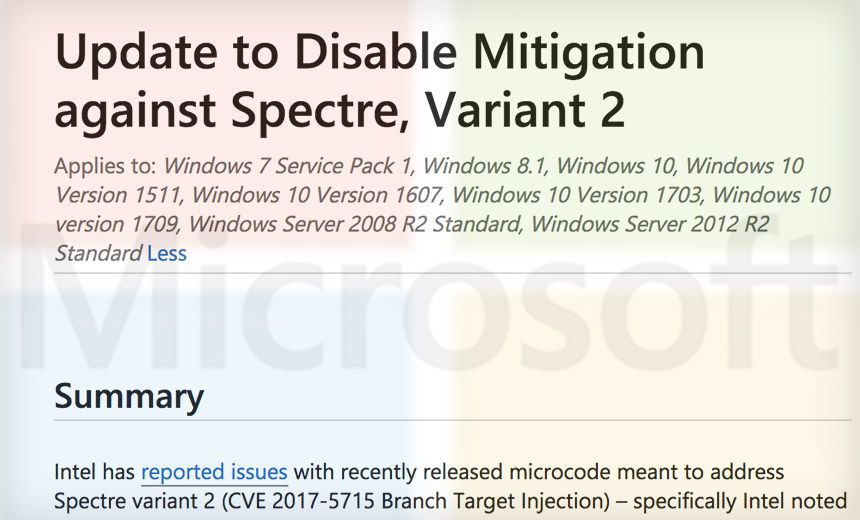
Then on Saturday, Microsoft released a security update enabling users and IT administrators to disable Intel's mitigation for Spectre variant 2, a branch target injection flaw designated CVE-2017-5715.
"Intel noted that this microcode can cause 'higher than expected reboots and other unpredictable system behavior' and then noted that situations like this may result in 'data loss or corruption,'" Microsoft says in its security update (see Intel: Stop Installing Patches Due to Reboot Problems).
"Our own experience is that system instability can in some circumstances cause data loss or corruption," Microsoft adds.
Intel says it's been working overtime with a number of other business partners -including Dell, HPE, HPI, Lenovo and Microsoft - to develop, test and distribute fixed firmware.
Pending the arrival of those fixes, however, Microsoft's out-of-band security update, designated KB4078130, will disable Intel's fix for CVE-2017-5715. Microsoft says its testing has found that applying its update eliminates the stability problems - and potential data loss and corruption - that Intel's firmware patch has been causing.
For "advanced users," Microsoft is also offering another option: the ability to manually enable or disable the fix for Spectre Variant 2 (CVE 2017-5715) "independently via registry setting changes." It has issued instructions aimed both at IT professionals working with endpoints as well as server administrators.
Disabling or not installing a fix for Spectre variant 2 should be considered a temporary strategy, Microsoft says. "As of January 25, there are no known reports to indicate that this Spectre variant 2 (CVE-2017-5715) has been used to attack customers," Microsoft says. "We recommend Windows customers, when appropriate, re-enable the mitigation against CVE-2017-5715 when Intel reports that this unpredictable system behavior has been resolved for your device."
Intel's Patch Alert
Microsoft's move follows Intel last week warning users that many of the firmware updates it had released for Spectre were causing instability problems - including frequent rebooting. Many different generations of Intel chips were suffering such problems, including its latest processors, codenamed Ivy Bridge, Sandy Bridge, Skylake, Kaby Lake, Broadwell and Haswell.
Until Intel releases fixes, Navin Shenoy, executive vice president and general manager of Intel's Data Center Group, on Jan. 22 recommended that "OEMs, cloud service providers, system manufacturers, software vendors and end users" - in short, everyone - "stop deployment of current versions, as they may introduce higher than expected reboots and other unpredictable system behavior."
A five-page guide from Intel, most recently updated Thursday, details which firmware should be avoided and for which specific processors.
Numerous Spectre, Meltdown Updates Required
Beyond Intel, some chips manufactured by AMD and ARM will also require firmware fixes to protect them from Spectre or Meltdown flaws (see Spectre Reversal: AMD Confirms Chips Have Flaws).
Apple, Cisco, Dell, Fujitsu, Google, IBM, Juniper, Oracle as well as Microsoft are among the many other vendors that must also update users' firmware and operating systems with Meltdown and Spectre protections.
.png?width=950&height=450&name=OneSafePlaceGlowandOutline%20(1).png)