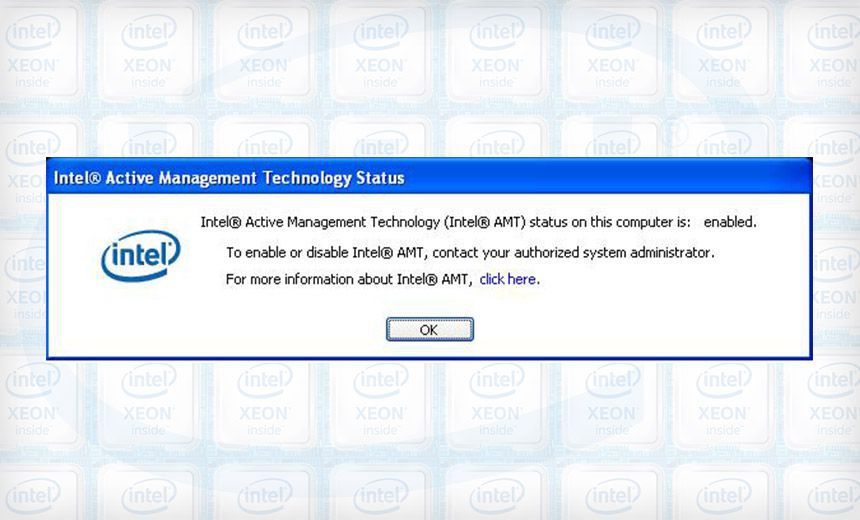
An attacker who gains physical access to a corporate PC with an Intel chip could exploit the built-in Active Management Technology to backdoor the system in about 30 seconds, unless default AMT credentials have been changed, Finnish security firm F-Secure warns.
"The attack is almost deceptively simple to enact, but it has incredible destructive potential," Harry Sintonen, a senior security consultant at F-Secure, says in a news release. "In practice, it can give a local attacker complete control over an individual's work laptop, despite even the most extensive security measures."
The attack would bypass any other security protections in place, including a BIOS password, Trusted Platform Module PIN or Bitlocker full-disk encryption,...
.png?width=950&height=450&name=OneSafePlaceGlowandOutline%20(1).png)